What is the SameSite cookie attribute?
In February 2020, Google Chrome began a rollout of a large change to the way cookies are transmitted that impacts session tracking. Cookies can specify a SameSite attribute, the value for which can be Lax (the default if nothing is explicitly specified), Strict or None.
With this change, cookies that need to be transmitted cross-site will need to have the SameSite attribute set to None AND specify a Secure attribute. Otherwise they will be ignored.
What does this change mean for my Heap tracking?
It’s important to note that Heap tracking code uses first-party cookies set by your domain. In most cases, the default value SameSite=Lax won’t have any impact on your Heap tracking, since the cookie isn’t transmitted cross-site.
Furthermore, Heap has taken the extra step of setting SameSite=None where it can be supported (SameSite=None can only be used in a secure context, ex. over HTTPS).
However, if you aren’t using HTTPs and are loading Heap differently (this scenario doesn’t apply to most users), you might see an impact. Especially if you are:
- Serving Heap over a file schema
- Launching Heap inside of an iframe
In this case, the Heap cookie would be considered as a cross-site cookie, and thus would fall under the scope of the SameSite update.
How can I ensure my Heap tracking is not impacted?
You might be impacted if you see spikes in sessions around February 2020: any navigation that might fall under the cross-site navigation category will cause the cookies to be reset because of the SameSite update, and sessions to increase abnormally.
If you believe you might be impacted or want to take extra precautions, make sure that you use the secureCookie option. With this option, cookies will be set in a secure context so will be defaulting to SameSite=None, and will continue to work as expected.
Why am I seeing SameSite cookie warnings in my browser console?
In October 2019, Chrome announced its intention to make security changes to third-party cookies. You can read more about it in this Chromium blog post.
Heap’s tracking code uses first-party cookies set by your domain and thus is not affected.
However, Heap, like many companies, uses products that store third-party cookies on Heap’s domain. If you use the Heap app and then visit your own site, you may see warnings like the following in your browser console.
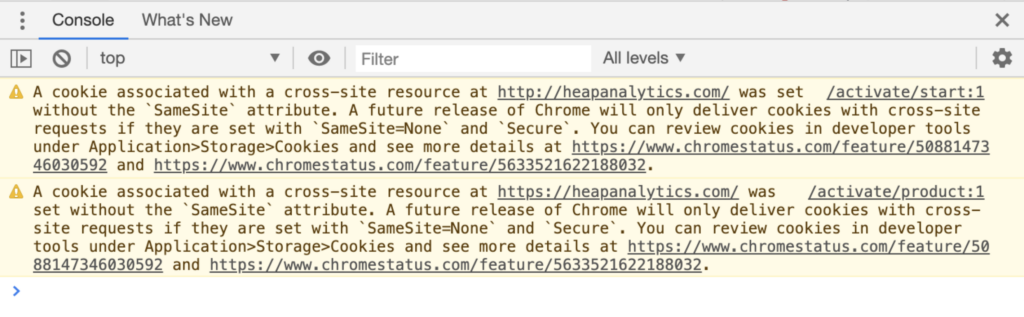
Please note that your customers should never see this message, unless they, too, are Heap customers.
We are exploring technical changes to avoid these warnings. However, this does not affect Heap tracking at all, and can be safely ignored.