Overview
Security Best Practice
If you use SSO, we strongly recommend that you set up mandatory 2FA for all Heap admins.
To learn more, see enabling mandatory 2FA for your Heap domain.
AWS SSO enables you to centrally manage SSO access and user permissions for all of your AWS accounts. No additional setup is required within the individual accounts; AWS SSO configures and maintains all of the necessary permissions in your accounts automatically.
Prerequisites
To set up AWS SSO access to Heap, you’ll need to have the following:
- Admin access to your organization’s Heap account
- Access to the AWS SSO console with IAM permissions to manage applications
Setup
Note that once SSO is enabled, it will be enforced as mandatory for all non-Admins in your Heap workspace.
To enable SSO for AWS, complete these steps:
1. On the AWS SSO Configure page, in the Details section, fill in the Display name and the Description (optional) of the application. We suggest that you choose a unique display name if you plan to have more than one of the same application.
2. Login to your Heap account as an Admin.
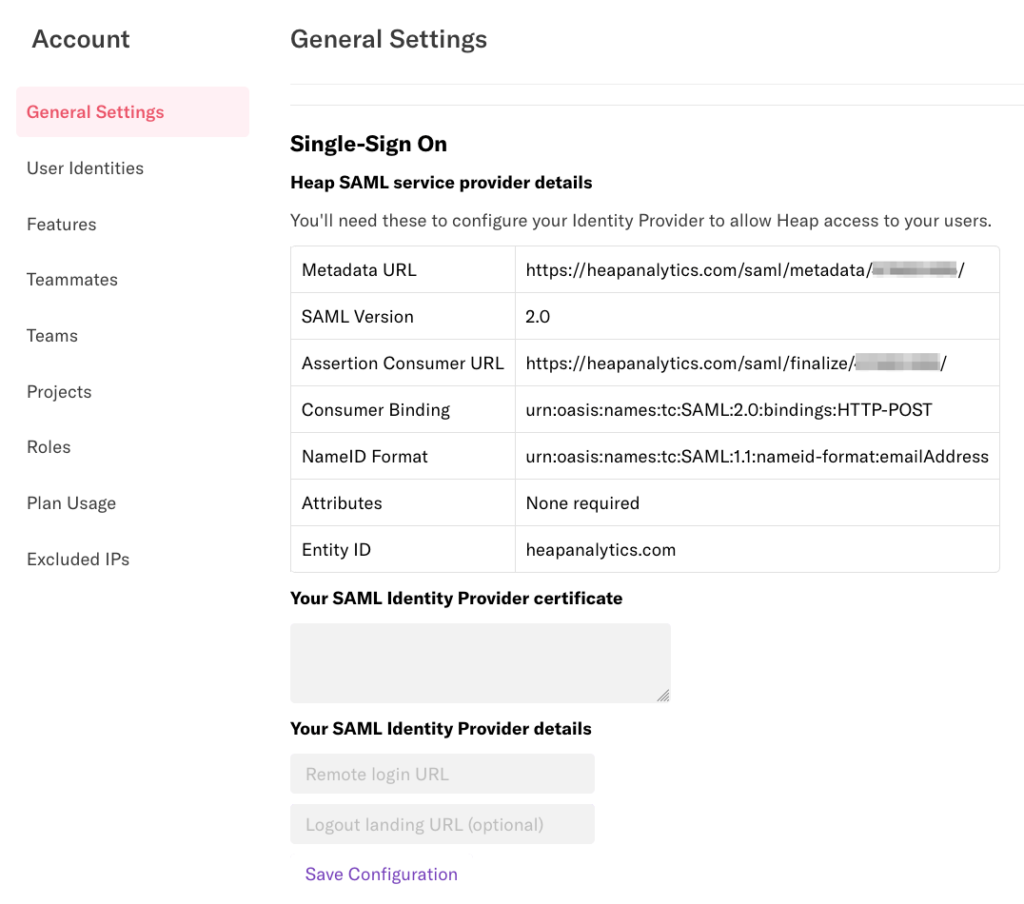
3. Navigate to Account > Manage > Account settings and scroll down to the Single Sign-On section. You’ll need the information listed here to configure AWS to allow Heap access.
5. Return to the AWS SSO console page.
6. Copy the AWS SSO sign-in and AWS SSO sign-out URLs, then download the AWS SSO certificate. Edit the downloaded certificate in a text editor to copy all its content.
7. Back in your Heap Account Settings, paste the AWS SSO sign-in URL into the Remote login URL of the SAML Identity Provider details section, paste AWS SSO sign-out into Logout landing URL (optional) and paste AWS SSO certificate content into Your SAML Identity Provider certificate** section.
8. Click Save Configuration at the bottom.
9. Return to the AWS SSO console page, and under Application metadata, choose specify configuration values individually to display the application metadata settings.
10. Copy and paste the value from Heap Single Sign-on‘s Assertion Consumer URL to Application ACS URL, copy and paste the value from Heap Single Sign-on‘s Entity ID to Application SAML audience.
| Field | Value |
| Application ACS URL | https://heapanalytics.com/saml/finalize/<your-app-id-goes-here>/ |
| Application SAML audience | heapanalytics.com |
11. In the AWS SSO console, Attribute mappings of your Heap application.
12. Input ${user:email} into Maps to this string value or user attribute in AWS SSO of Subject, select emailAddress.
13. Create another User attribute in the application with name as NameId, Input ${user:email} into Maps to this string value or user attribute, select unspecified.
14. Click on Save Changes.
15. Assign a user to the application in Application‘ s Assinged users of AWS SSO console.
16. Return to the Heap Account Settings page where you are configuring SSO, and click Test Provider.
17. Input your Heap admin user email and password.
18. You will be redirected to AWS SSO log-in page; input your AWS SSO AD username and password. The user must be an existing teammate in Heap.
19. If successful, Click on Enable Provider.
19. From your Heap Account Settings, click Invite your Teammates to send invitations to your team member’s email address. Otherwise, they will not be able to log in via SSO.
Documentation
For general troubleshooting, please refer to the AWS Troubleshooting Guide.