Overview
Security Best Practice
If you use SSO, we strongly recommend that you set up mandatory 2FA for all Heap admins.
To learn more, see enabling mandatory 2FA for your Heap domain.
Okta SSO allows you to provide secure identity management for your team in Heap using one of the most popular enterprise access management tools available on the market today. Okta offers ease of access, the ability to quickly block credentials for departed team members, multi-factor authentication, and more.
Prerequisites
To set up Okta SSO with Heap, you’ll need to have the following:
- Admin access to your organization’s Heap account
- Administrator rights in your organization’s Okta account
Setup
Note that once SSO is enabled, it will be enforced as mandatory for all non-Admins in your Heap workspace.
To set up SSO via Okta, complete these steps:
1. Login to your Okta account
2. Click Admin

3. Navigate to the Applications section
4. Click Browse App Catalog

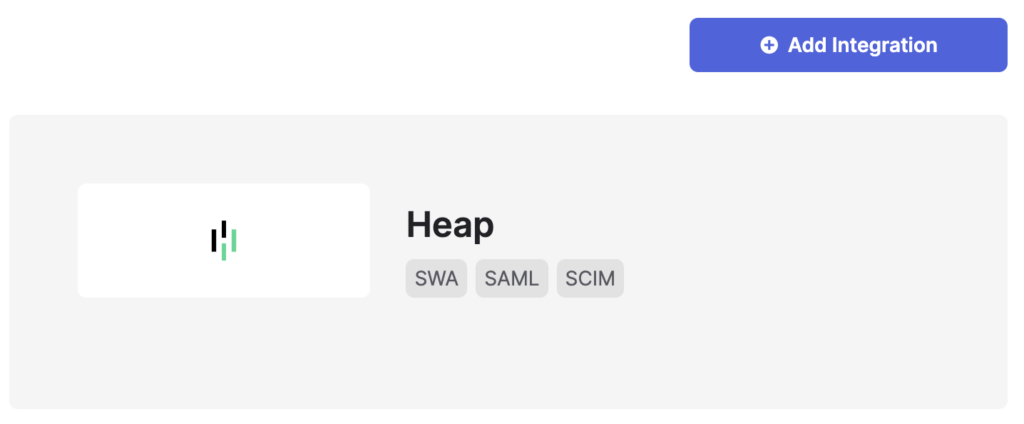
5. Search for Heap, select the Heap application, and click Add Integration
6. Name the app (such as ‘Heap’), then click Next
7. Open the Heap dashboard in a new tab and navigate to Account > Manage > Account settings then scroll down to the Single Sign-On section
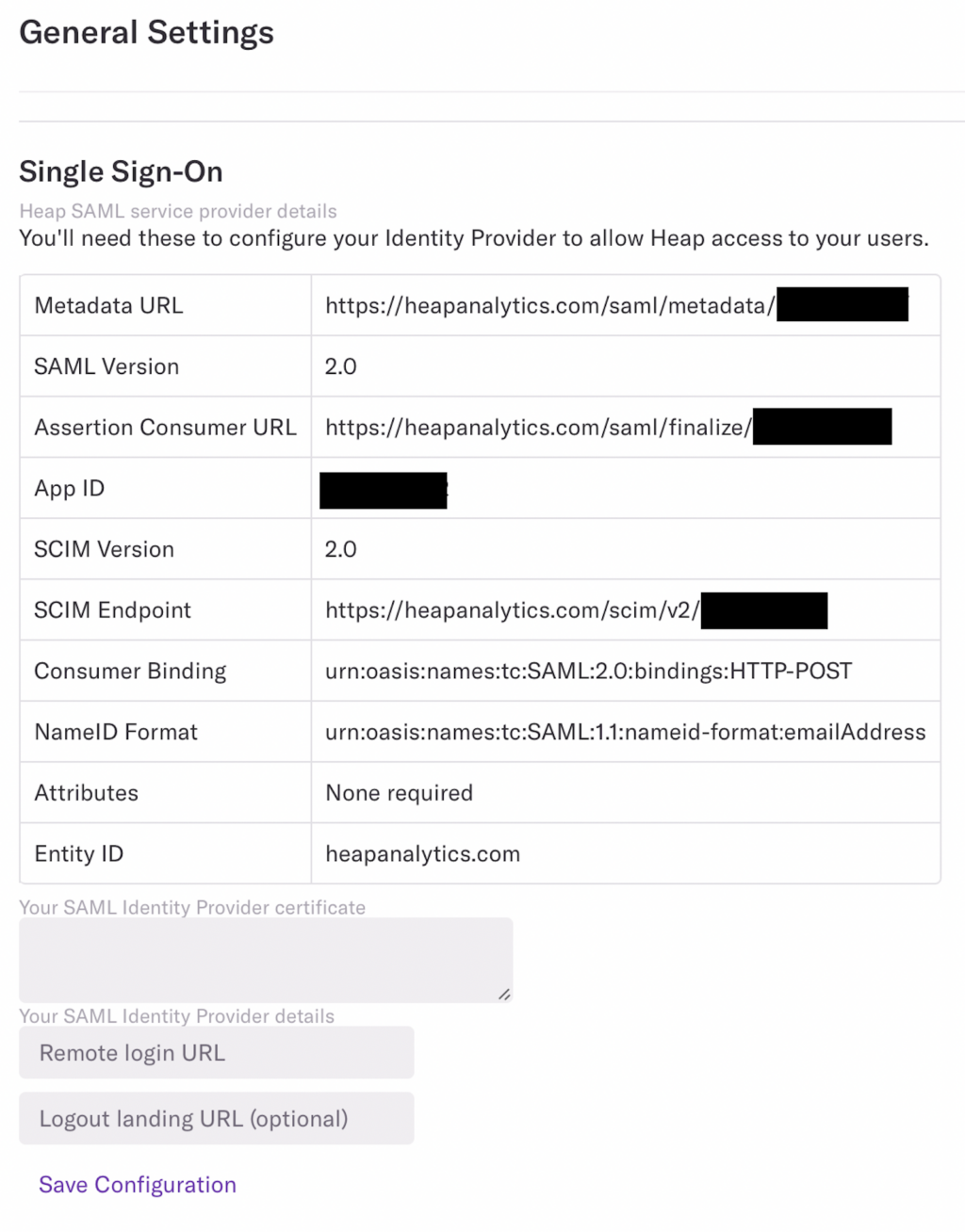
8. Copy the App ID from Heap into the App ID field in Okta
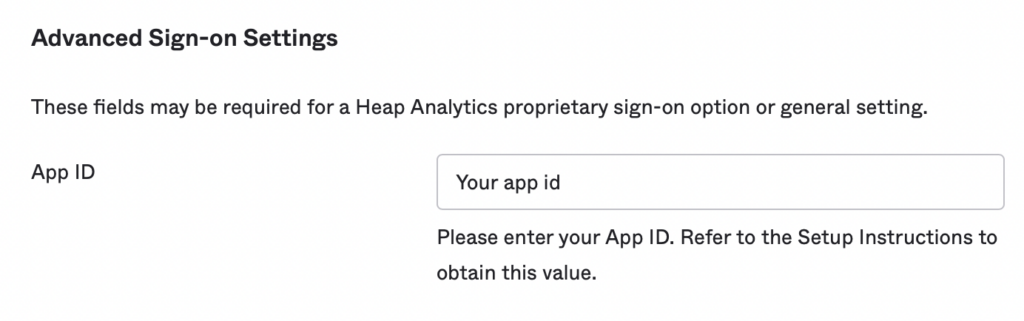
9. Update the Application username format to Email
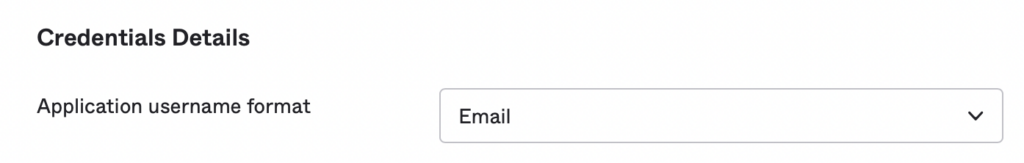
10. Click Done
11. Under the Sign on methods section, click More details to show the Sign on URL. Copy paste it somewhere safe to use in a future step.
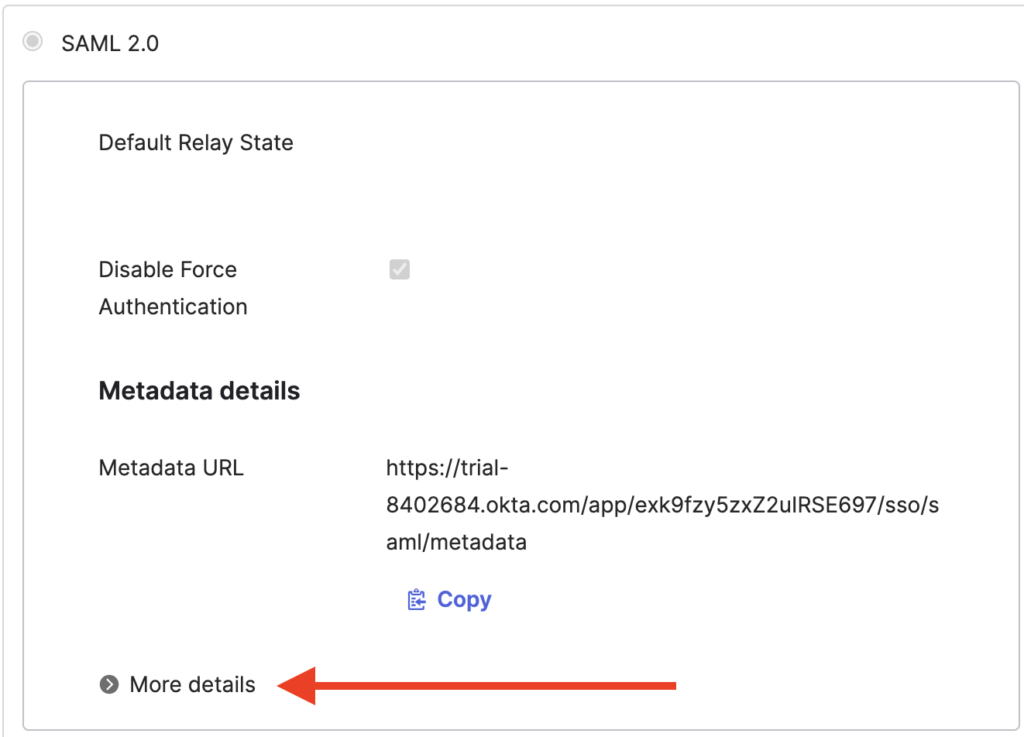
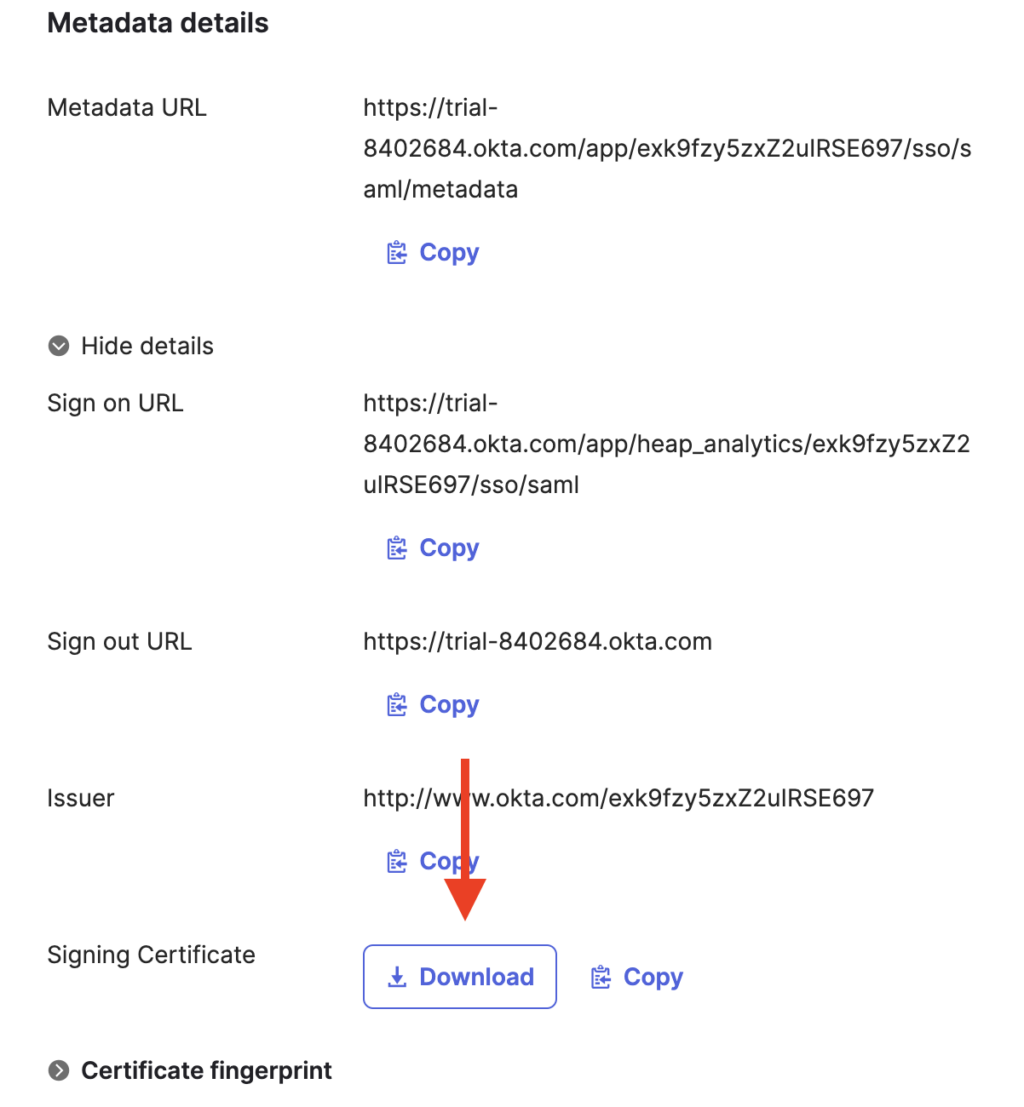
12. Still in the Sign on methods section, click the download button to download the certificate
Note: If you’re on a Mac, clicking Open from your browser may result in it trying to open the file in keychain, which will not allow you to access the contents of the file. To avoid this, navigate to your Downloads folder, select the file, and then open it in a standard text editor (TextEdit will work).
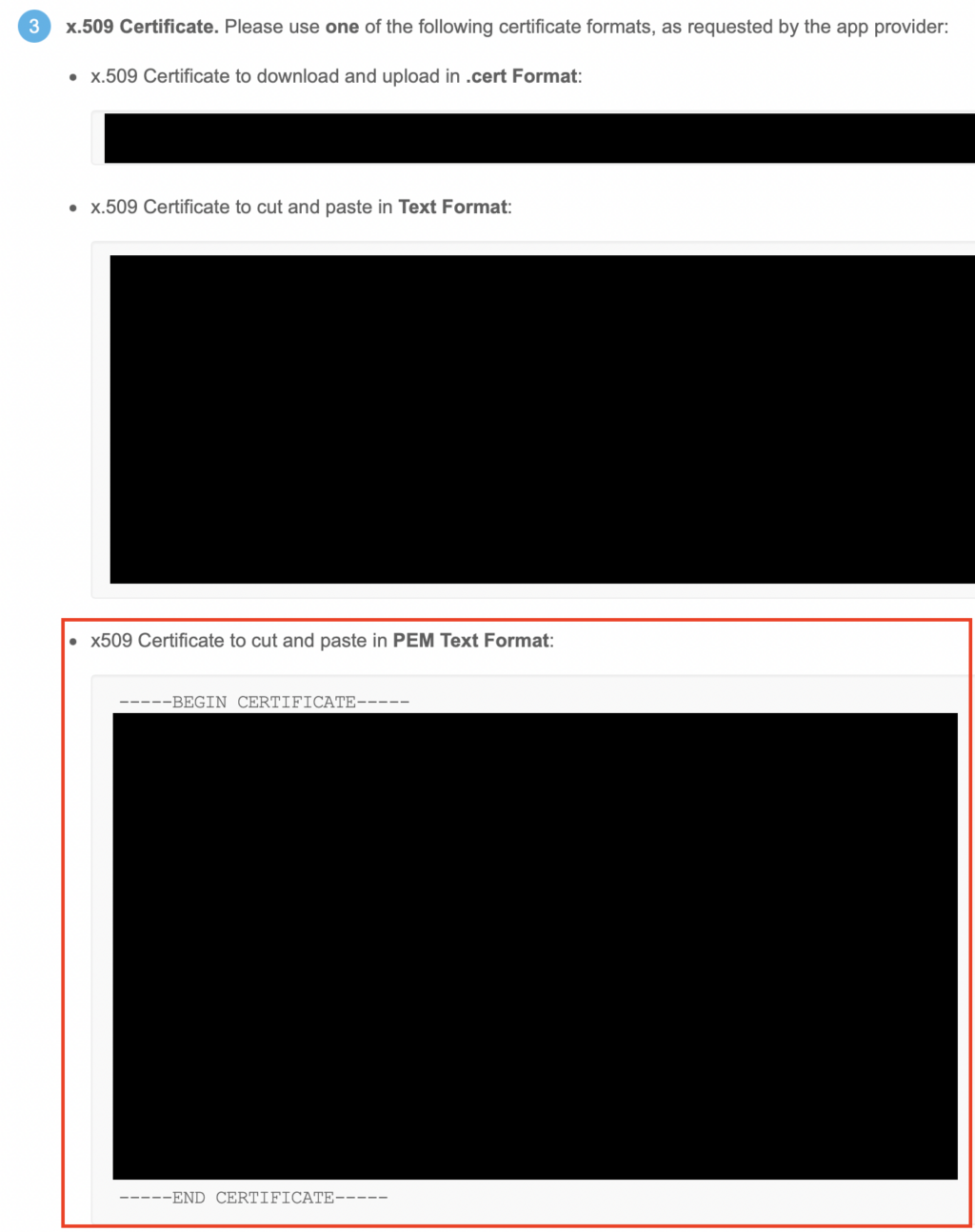
13. Copy the x.509 certificate in PEM Text Format including Begin Certificate and End Certificate and paste it back into the Your SAML Identity Provider certificate field in Heap
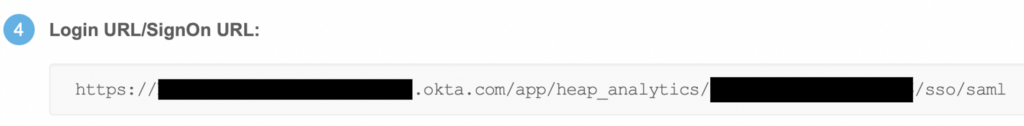
14. Copy the Login URL/SignOn URL from Okta and paste it back into Heap’s Remote Login URL within the Your SAML Provider details area
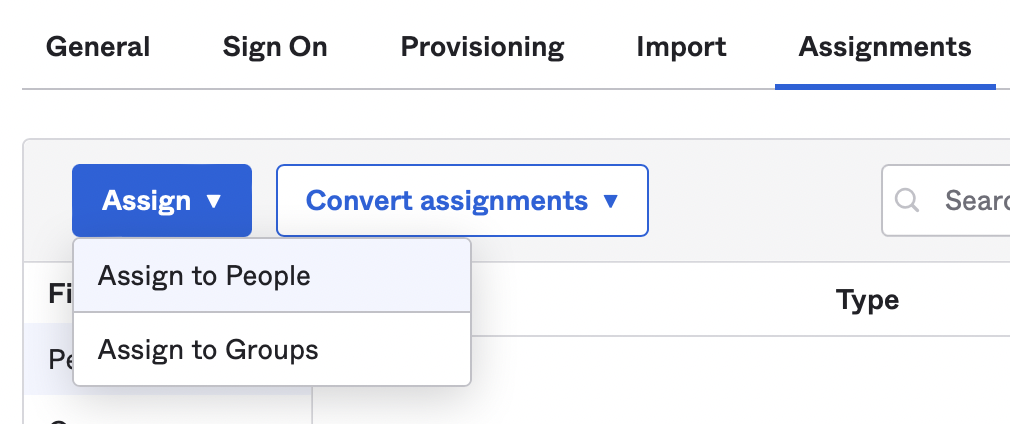
15. Add teammates in Okta who you want to grant access to Heap (or at a minimum, add yourself)
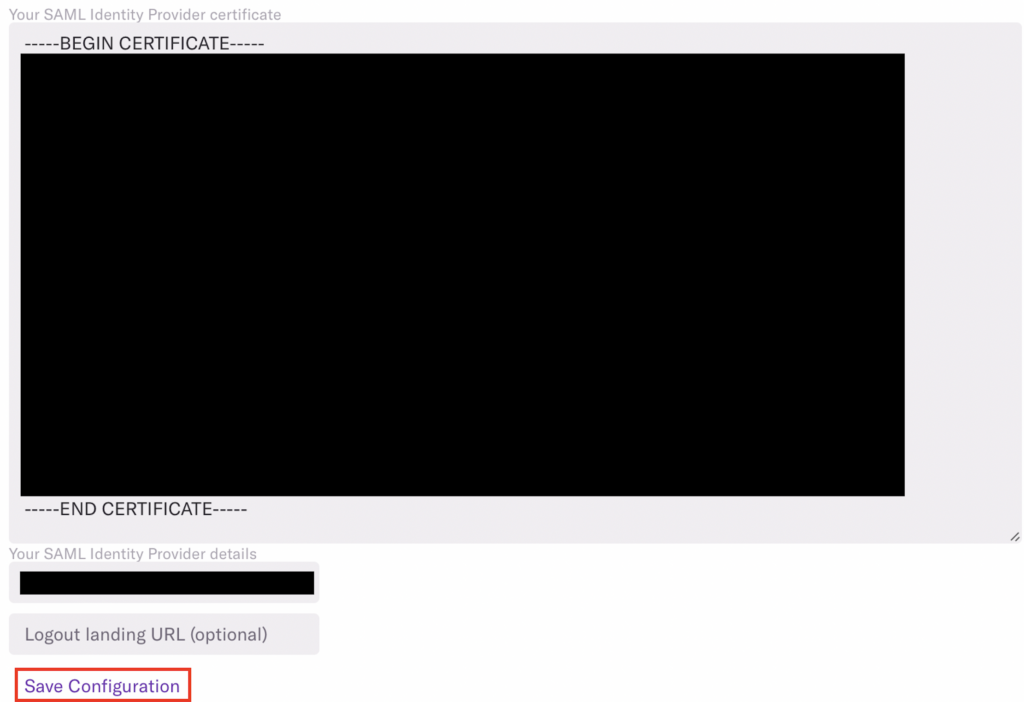
16. Back in Heap, click on Save Configuration then Test Configuration – if everything is working properly, this should redirect you back to Heap!
17. Last but not least, click Enable Configuration, then add additional teammates as needed
Once configured, your teammates can select Sign-in with SSO on the Heap login page, and log in with their email address only. Admins will still have access to sign in with an email and password combination, while all other users will be pushed to use SSO.
Troubleshooting
If you are having issues logging in with Okta SSO, please delete the Okta cookie and try again. Currently, we are seeing Okta cookies expiring and not allowing proper login. If deleting the cookie doesn’t work, please contact us via the Get support page in Heap.